Are Important Because They Help To Ensure Data Integrity.
Larn nearly data integrity, information integrity vs. data security, and more in Data Protection 101, our serial on the fundamentals of data protection.
A DEFINITION OF DATA INTEGRITY
Information integrity refers to the accuracy and consistency (validity) of data over its lifecycle. Compromised data, after all, is of little use to enterprises, not to mention the dangers presented past sensitive information loss. For this reason, maintaining data integrity is a core focus of many enterprise security solutions.
Information integrity tin be compromised in several means. Each time data is replicated or transferred, it should remain intact and unaltered between updates. Error checking methods and validation procedures are typically relied on to ensure the integrity of data that is transferred or reproduced without the intention of alteration.
DATA INTEGRITY AS A Procedure AND AS A Country
The term data integrity also leads to confusion because information technology may refer either to a state or a process. Data integrity as a country defines a data set that is both valid and accurate. On the other paw, information integrity as a process, describes measures used to ensure validity and accuracy of a data set or all information contained in a database or other construct. For instance, fault checking and validation methods may be referred to as data integrity processes.
A Example FOR Information INTEGRITY
Maintaining data integrity is of import for several reasons. For one, data integrity ensures recoverability and searchability, traceability (to origin), and connectivity. Protecting the validity and accuracy of data likewise increases stability and performance while improving reusability and maintainability.
Data increasingly drives enterprise controlling, but it must undergo a variety of changes and processes to become from raw form to formats more applied for identifying relationships and facilitating informed decisions. Therefore, information integrity is a top priority for mod enterprises.
Data integrity can be compromised in a variety of ways, making data integrity practices an essential component of effective enterprise security protocols. Data integrity may be compromised through:
- Human error, whether malicious or unintentional
- Transfer errors, including unintended alterations or data compromise during transfer from one device to another
- Bugs, viruses/malware, hacking, and other cyber threats
- Compromised hardware, such as a device or disk crash
- Physical compromise to devices
Since only some of these compromises may exist adequately prevented through information security, the case for data backup and duplication becomes critical for ensuring data integrity. Other data integrity best practices include input validation to preclude the entering of invalid data, error detection/data validation to identify errors in data transmission, and security measures such as data loss prevention, admission command, data encryption, and more than.
Information INTEGRITY FOR DATABASES
In the broad sense, data integrity is a term to understand the health and maintenance of any digital data. For many, the term is related to database direction. For databases, there are four types of data integrity.
- Entity Integrity: In a database, there are columns, rows, and tables. In a primary key, these elements are to be as numerous as needed for the data to exist accurate, yet no more than than necessary. None of these elements should be the same and none of these elements should be null. For instance, a database of employees should have primary key data of their name and a specific "employee number."
- Referential Integrity: Foreign keys in a database is a second table that can refer to a main key table within the database. Foreign keys relate data that could be shared or zippo. For instance, employees could share the aforementioned role or work in the same department.
- Domain Integrity: All categories and values in a database are set, including nulls (e.g., N/A). The domain integrity of a database refers to the common means to input and read this data. For instance, if a database uses monetary values to include dollars and cents, three decimal places will not exist allowed.
- User-Divers Integrity: There are sets of data, created by users, outside of entity, referential and domain integrity. If an employer creates a column to input cosmetic action of employees, this data would exist classified as "user-defined."
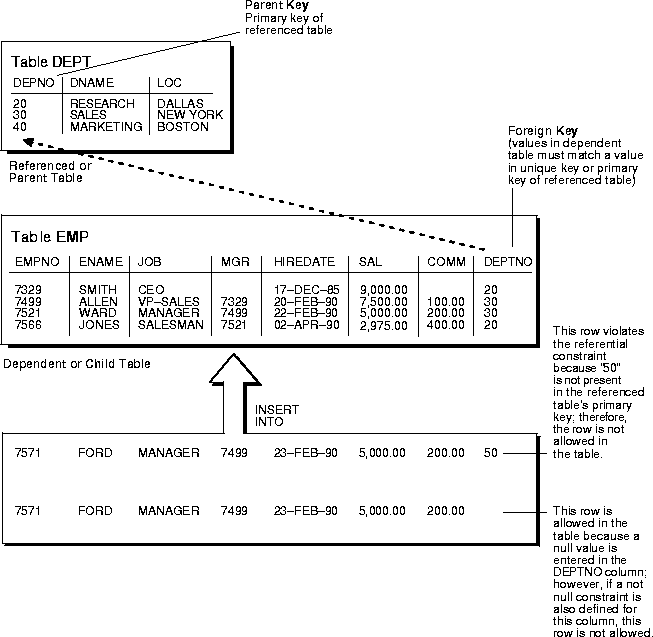
Image Source: Oracle
Information INTEGRITY VS. Information SECURITY
Data integrity and data security are related terms, each playing an of import role in the successful achievement of the other. Information security refers to the protection of data against unauthorized admission or abuse and is necessary to ensure data integrity.
That said, data integrity is a desired result of data security, but the term data integrity refers just to the validity and accuracy of data rather than the human activity of protecting data. Data security, in other words, is i of several measures which tin can be employed to maintain information integrity. Whether it'due south a instance of malicious intent or accidental compromise, information security plays an important role in maintaining information integrity.
For modern enterprises, data integrity is essential for the accuracy and efficiency of business processes equally well as decision making. It'due south as well a central focus of many information security programs. Achieved through a variety of data protection methods, including backup and replication, database integrity constraints, validation processes, and other systems and protocols, information integrity is disquisitional nonetheless manageable for organizations today.
Are Important Because They Help To Ensure Data Integrity.,
Source: https://digitalguardian.com/blog/what-data-integrity-data-protection-101
Posted by: baxteralthe1967.blogspot.com


0 Response to "Are Important Because They Help To Ensure Data Integrity."
Post a Comment